Enhance Google Chrome with features for speed and productivity
Is Google Chrome draining your computer’s memory and slowing you down? Recent updates have introduced powerful built-in tools designed to boost performance, no complicated fixes

Is Google Chrome draining your computer’s memory and slowing you down? Recent updates have introduced powerful built-in tools designed to boost performance, no complicated fixes

Disaster recovery isn’t just an IT checklist item — it’s a business survival strategy. This article breaks down persistent myths and outlines what leaders need

Tired of managing endless passwords across your business apps? Single sign-on (SSO) offers a secure, streamlined solution that improves productivity while strengthening protection. Here’s why

Protecting sensitive information is the core purpose of the Health Insurance Portability and Accountability Act (HIPAA). HIPAA mandates that patients have full control over access
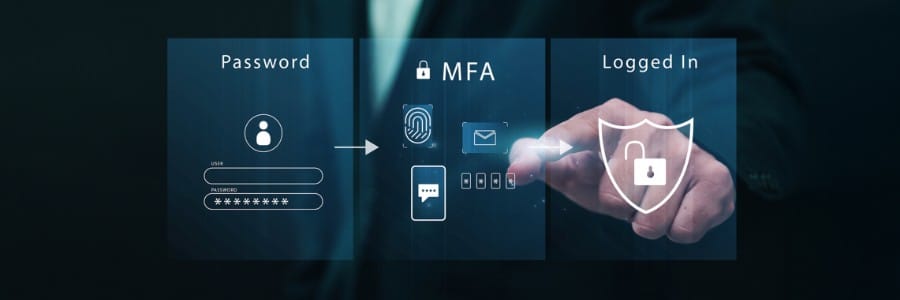
Multifactor authentication (MFA) works by requiring users to provide more than one form of identification when logging into a system or account. This extra layer

Imagine a customer walking into your physical store, looking around for five seconds, and then immediately walking out without saying a word. The same thing

Cyberattacks, technical failures, or simple human error can creep up out of nowhere. And when they occur, businesses are often left scrambling to recover lost

Cybersecurity experts Rob Wright (Dark Reading), David Jones (Cybersecurity Dive), and Alissa Irei (TechTarget Search Security) recently came together to discuss the future of online

Cloud computing is the use of remote servers to store, manage, and process data, freeing businesses from the limits of physical infrastructure. For small businesses,

Your bathroom, your kitchen table, even your dreams — if it’s part of your life, health tech wants in. CES 2026, the world’s biggest technology